Cybersecurity is a vast and complex field that calls on many tools and techniques to protect systems and data against cyberthreats. One of the main tools used in cybersecurity is the playbook, which is a set of predefined procedures and steps for responding to specific types of incidents or vulnerabilities. A playbook can help security teams deal quickly and effectively with common or emerging cyber attacks, such as phishing, ransomware, denial of service or data breaches.
A playbook typically consists of the following elements:
A trigger or condition that activates the playbook, such as an alert, report or query.
A scope or objective that defines the purpose and limits of the simulation, such as the system, service or data involved.

A scope or objective that defines the purpose and limits of the simulation, such as the system, service or data involved.
A workflow or process that describes the sequence of actions and tasks to be performed by the safety team, such as identification, analysis, containment, eradication, recovery and post-incident activities.
A checklist or template that provides detailed instructions and guidance for each action and task, such as tools, commands, scripts, evidence collection, communication, escalation and documentation.
A playbook can also include additional information and resources, such as roles and responsibilities, contact details, references, best practice, lessons learned and feedback.
Security is everyone’s responsibility and for any organization, the focus should be to educate their employees about the different types of security attacks and how to ensure that security is not compromised.
Here are some examples of cybersecurity playbooks:
Incident response manuals: These are manuals that help security teams respond to cyber attacks that have already taken place or are in progress. They aim to minimize the impact and damage of the incident, restore normal operations as quickly as possible and prevent the incident from happening again. Microsoft Learn, CISA, NIST and Atlassian are sources of incident response manuals.
Vulnerability response manuals: These are manuals that help security teams respond to vulnerabilities that have been discovered or reported in their systems or applications. Their purpose is to assess the risk and severity of the vulnerability, apply patches or mitigation measures if necessary, and monitor any attempted exploitation. CISA and NIST are sources of vulnerability response manuals.
The APT lifecycle is a term that describes the stages of an advanced persistent threat (APT), i.e. a stealthy and sophisticated cyber attack that aims to steal or damage sensitive data or systems. The lifecycle of an APT generally consists of the following phases:
– Reconnaissance: The attacker gathers information about the target organisation, such as its network structure, security defences, employees and vulnerabilities. A variety of techniques can be used, such as open source information, social engineering, phishing or scanning.
– Initial compromise: the attacker exploits a vulnerability or human error to gain initial access to the target network. They can use a variety of techniques, such as malware, zero-day exploits, theft of credentials or insider threats.
– Establishing a foothold: The attacker installs tools or malware on the compromised system to maintain permanent access and communicate with the command and control server. They can use a variety of techniques, such as backdoors, rootkits, keyloggers or remote access Trojans.
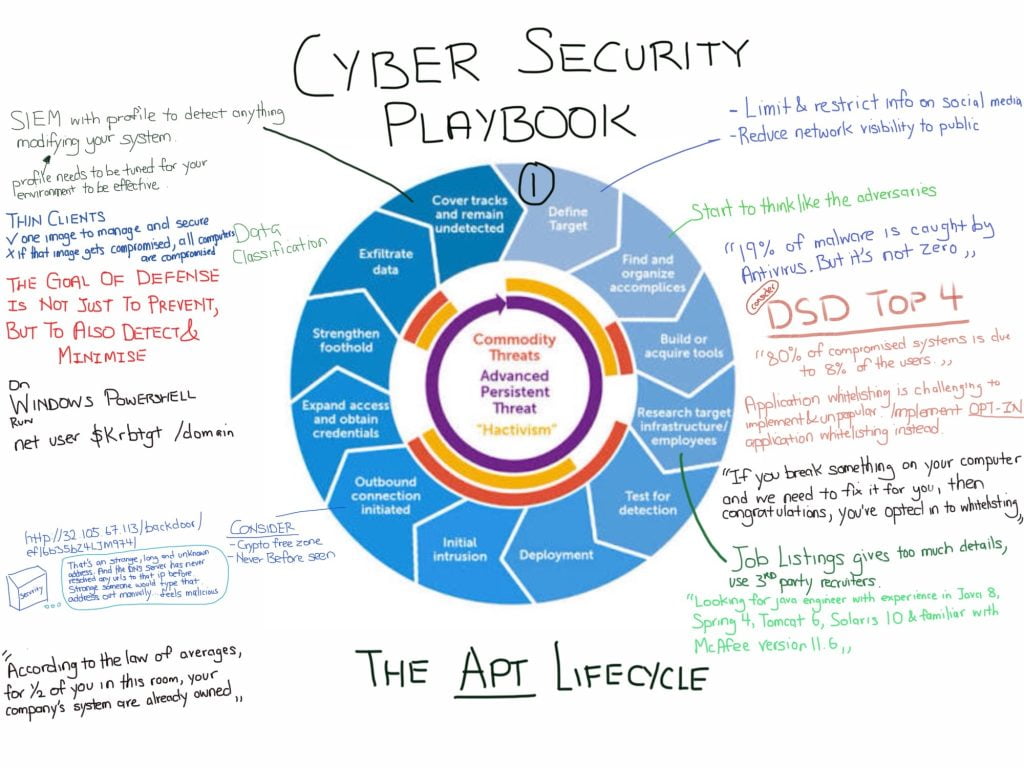
Lateral movement: The attacker moves across the target network to find and access the desired data or systems. They can use a variety of techniques, such as privilege escalation, pass-the-hash, lateral movement frames or stealing credentials.
Data exfiltration: The attacker collects and transfers data or systems to an external site. Various techniques can be used, such as encryption, compression, steganography or covert channels.
Covering traces: The attacker erases or modifies all traces of his presence or activity on the target network. They can use a variety of techniques, such as deleting logs, erasing files or planting false evidence.
The lifecycle of an APT can vary depending on the attacker’s specific objectives, tactics and techniques. However, it generally follows a similar pattern of reconnaissance, compromise, persistence, movement, exfiltration and concealment.