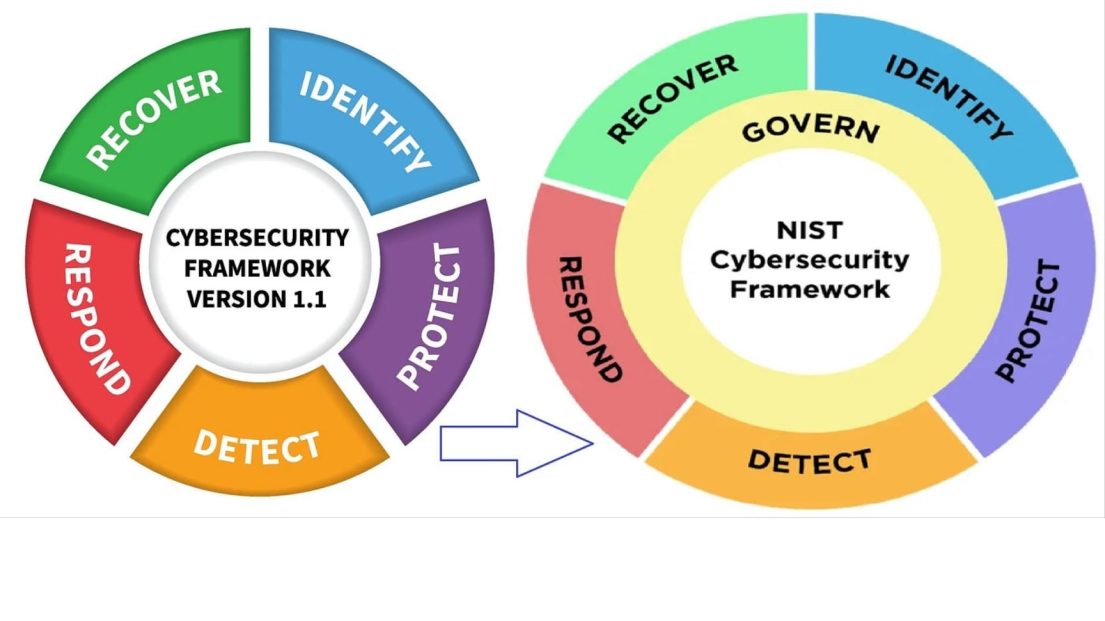
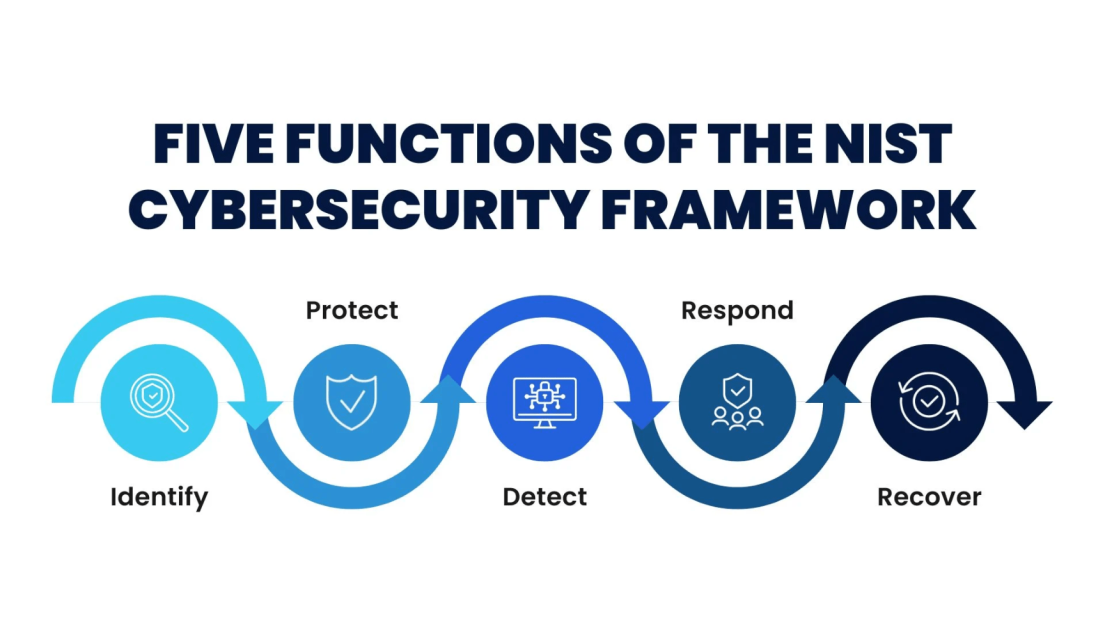
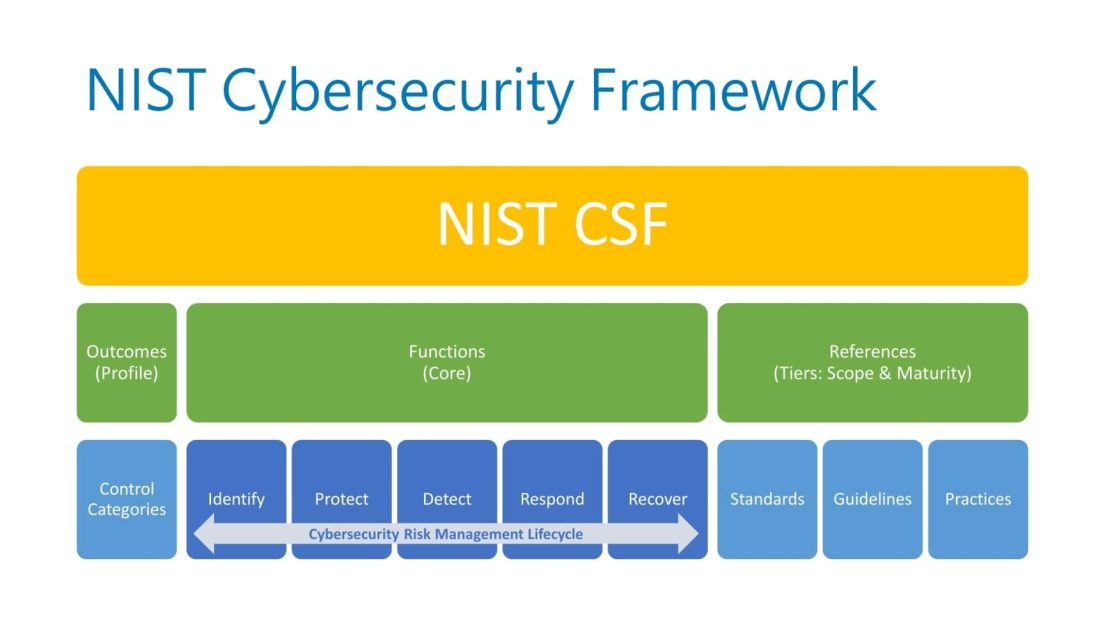
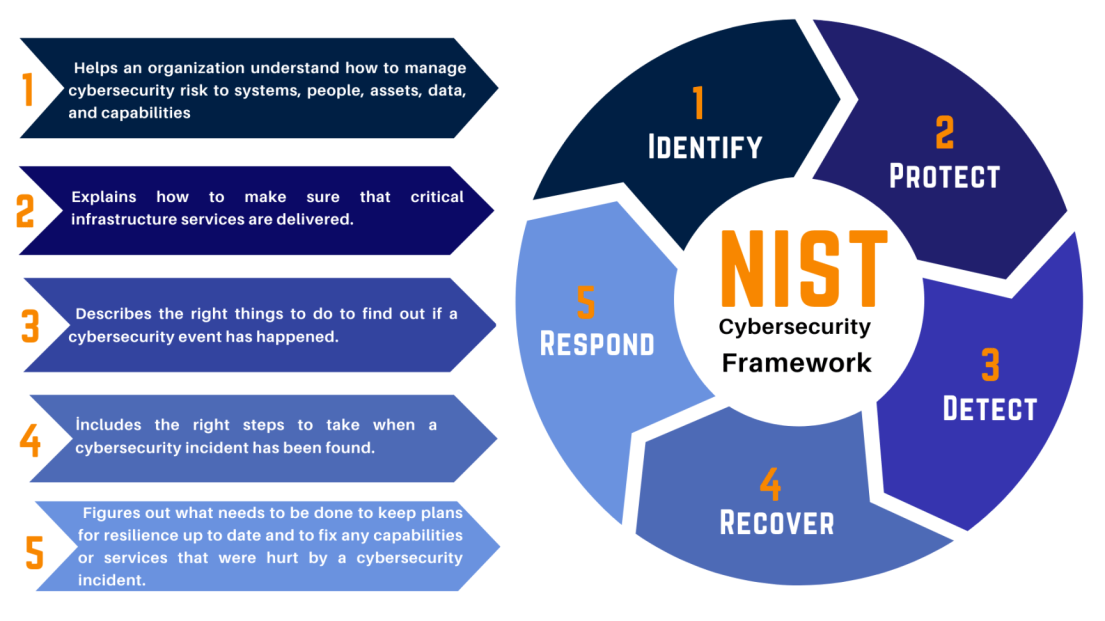
Penetration testing tools
Penetration testing tools can help improve security posture, test security defenses, and comply with security standards.
Data-centric security
Data-centric security can help encrypt, mask, tokenize, or anonymize data to ensure its confidentiality, integrity, and availability.