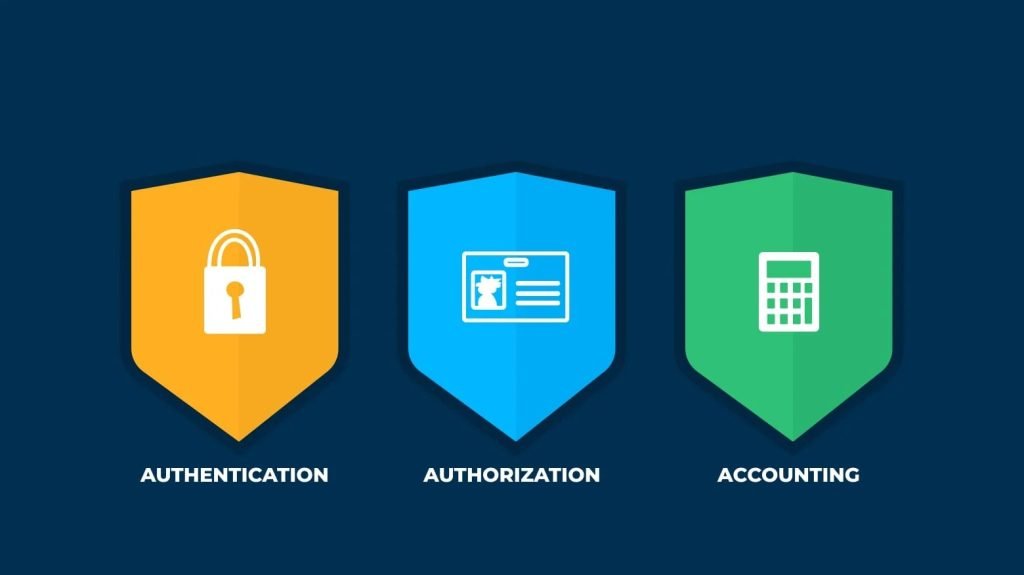

Authentication, authorization, and accounting (AAA) is a security framework that controls access to computer resources, enforces policies, and audits usage. AAA and its combined processes play a major role in network management and cybersecurity by screening users and keeping track of their activity while they are connected.
Authentication involves a user providing information about who they are. Users present login credentials that affirm they are who they claim. As an identity and access management (IAM) tool, a AAA server compares a user’s credentials with its database of stored credentials by checking if the username, password, and other authentication tools align with that specific user.
The three types of authentication include something you know, like a password, something you have, like a Universal Serial Bus (USB) key; and something you are, such as your fingerprint or other biometrics.
Authorization follows authentication. During authorization, a user can be granted privileges to access certain areas of a network or system. The areas and sets of permissions granted a user are stored in a database along with the user’s identity. The user’s privileges can be changed by an administrator. Authorization is different from authentication in that authentication only checks a user’s identity, whereas authorization dictates what the user is allowed to do.
For example, a member of the IT team may not have the privileges necessary to change the access passwords for a company-wide virtual private network (VPN). However, the network administrator may choose to give the member access privileges, enabling them to alter the VPN passwords of individual users. In this manner, the team member will be authorized to access an area they were previously barred from.
Accounting keeps track of user activity while users are logged in to a network by tracking information such as how long they were logged in, the data they sent or received, their Internet Protocol (IP) address, the Uniform Resource Identifier (URI) they used, and the different services they accessed.
Accounting may be used to analyze user trends, audit user activity, and provide more accurate billing. This can be done by leveraging the data collected during the user’s access. For example, if the system charges users by the hour, the time logs generated by the accounting system can report how long the user was logged in to the router and inside the system, and then charge them accordingly.
Identification or Authentication: Confirming or denying the identity of the user attempting to access an asset. Single sign on (SSO) is a form of authentication. Authorization: Controlling what a user is able to do once they are operating within an enterprise asset. Role-based access controls (RBAC) are an example of an authorization approach.
Administration and Management: Provisioning and managing throughout the user account lifecycle—from setup to deactivation, as well as the administration and management of requirements related to compliance and regulation and access to different computing environments and architectures, including on-premise, software as a service (SaaS), UNIX, Windows, iOS, and Android.
Monitoring and Auditing: Observing, tracking, managing, and reporting on a user’s activities. The types of data and metrics that are often monitored or audited include password resets, uncorrelated accounts, number of accounts and associated roles and entitlements across applications and systems, login failures, uncorrelated privileged accounts, separation-of-duty violations, non-human identities and associated access.
Security and Protection: Protecting enterprise assets (corporate devices, systems, data, networks, or software applications) from threats, such as breaches and damage due to unauthorized access by external threat actors, as well as insiders, such as disgruntled employees.

JPCERT/CC is a valuable resource for organizations that are looking to improve their information security. By providing a variety of services, JPCERT/CC can help organizations to prevent, detect, and respond to computer security incidents.
Here are some of the things that JPCERT/CC does:
JPCERT/CC is a valuable resource for anyone who is interested in computer security. If you are a security professional, you can use JPCERT/CC’s resources to stay up-to-date on the latest security threats and to learn about new security technologies. If you are a business owner, you can use JPCERT/CC’s resources to improve your organization’s security posture. And if you are a student, you can use JPCERT/CC’s resources to learn about computer security and to get involved in the security community.
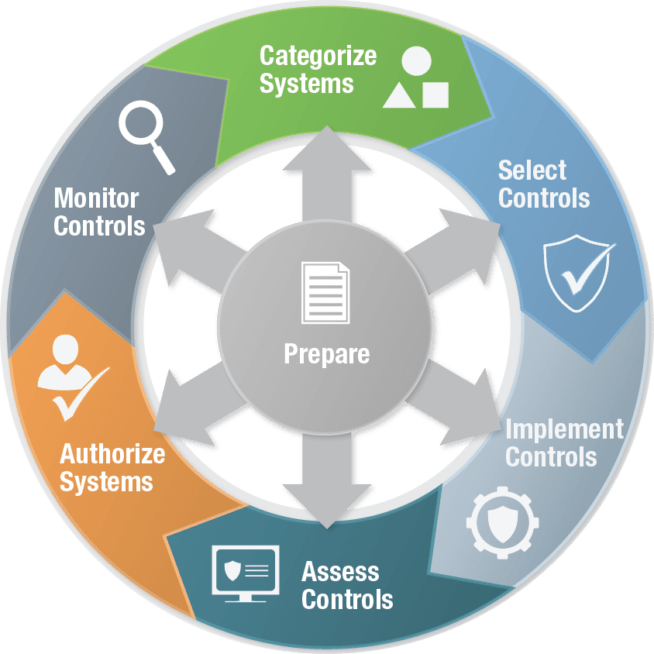
NIST RMF consists of the following 7 steps:
NIST RMF is a valuable tool for any organization that is looking to improve its information security. By following the NIST RMF, organizations can identify and mitigate risks to their information and systems, and improve their overall security posture.
Here are some of the benefits of using NIST RMF:
If you are looking for a way to improve your organization’s information security, NIST RMF is a valuable tool to consider.
IAM helps organizations to ensure that only authorized users have access to sensitive data and systems.
IAM typically includes the following features:
IAM is an important part of an organization’s overall security strategy. IAM can help organizations to protect their data and systems from unauthorized access.
Here are some of the benefits of implementing IAM:
IAM is a valuable tool for organizations of all sizes. IAM can help organizations to improve their security posture, increase their efficiency, and reduce their costs.