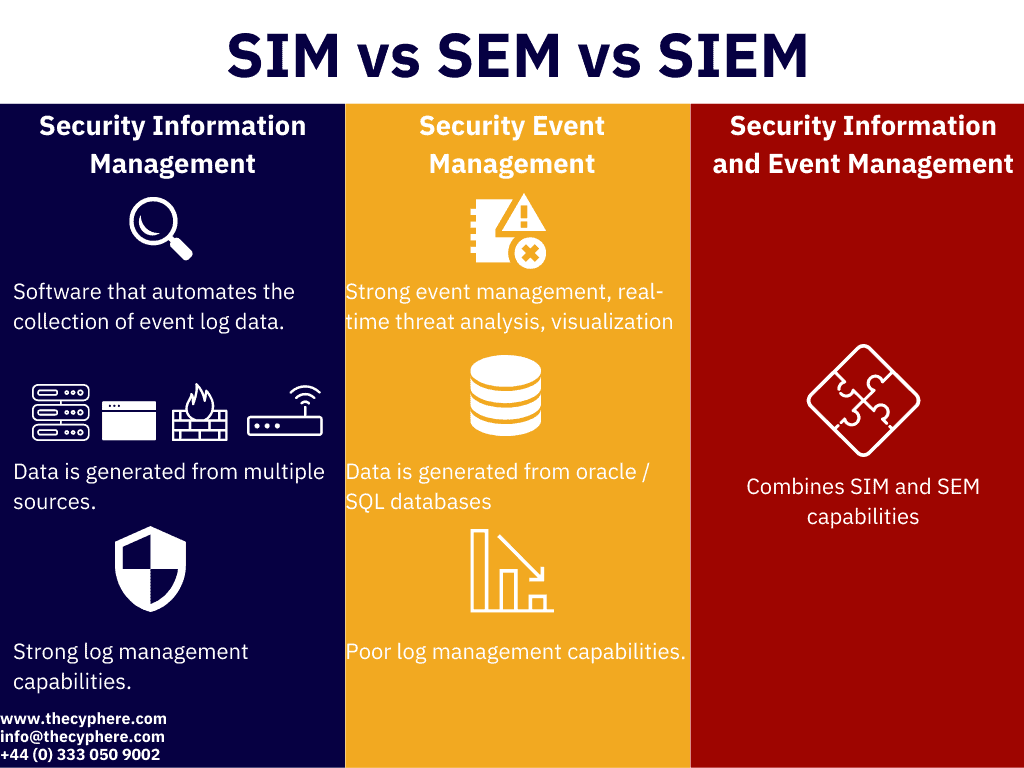
SIEM stands for Security Information and Event Management. It is a security solution that helps organizations detect, analyze, and respond to security threats before they harm business operations. SIEM combines both security information management (SIM) and security event management (SEM) into one security management system.
SIM collects and stores security logs from a variety of sources, such as firewalls, intrusion detection systems, and web servers. SEM analyzes these logs for suspicious activity, such as unauthorized access attempts or malware infections. SIEM takes SIM and SEM one step further by correlating the data from these two sources to identify patterns of behavior that may indicate a security breach.
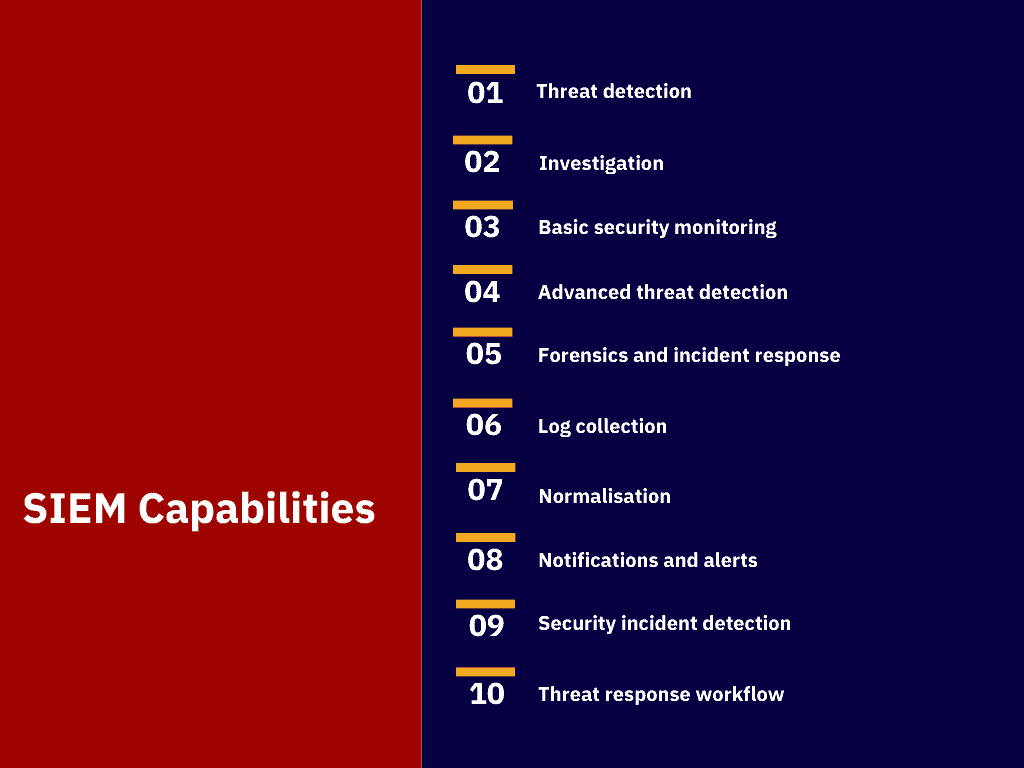
SIEM can be used to detect a wide range of security threats, including:
SIEM can also be used to comply with a variety of security regulations, such as PCI DSS, HIPAA, and SOX.
Here are some of the benefits of using a SIEM solution:
If you are looking for a way to improve your organization’s security posture, a SIEM solution is a great option. SIEM can help you detect, analyze, and respond to security threats before they cause damage to your business.
Here are some of the most popular SIEM solutions on the market:
When choosing a SIEM solution, it is important to consider your organization’s specific needs and requirements. Factors to consider include:
A SIEM solution can be a valuable asset for any organization that is looking to improve its security posture. By collecting, storing, and analyzing security data from a variety of sources, SIEM can help you detect and respond to security threats more quickly and effectively.
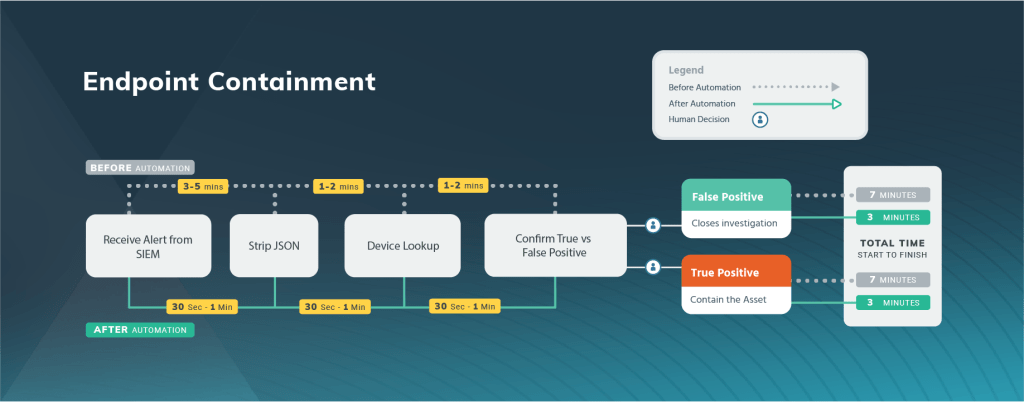
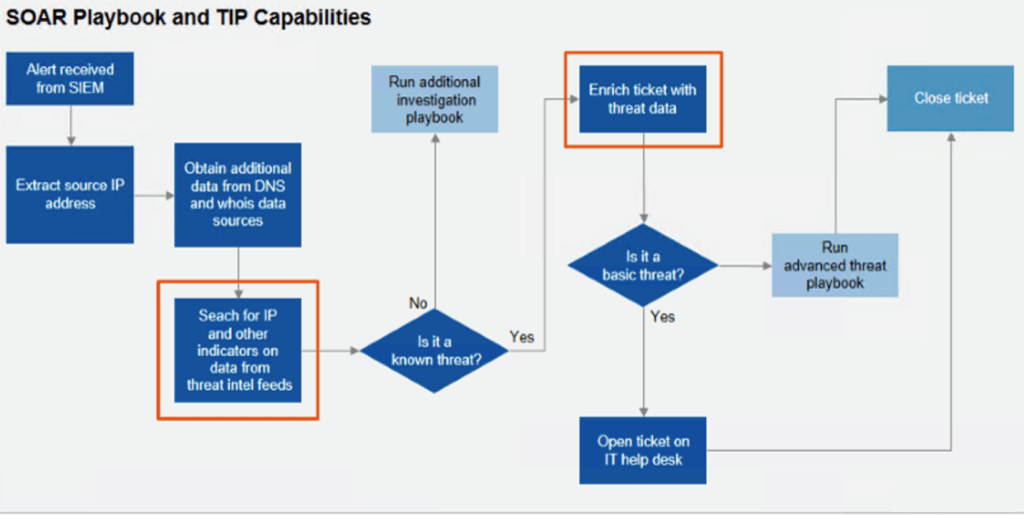
SOAR playbooks can be used to improve the efficiency and effectiveness of security operations by:
SOAR playbooks are a valuable tool for any organization that is looking to improve the efficiency and effectiveness of its security operations. By automating manual tasks, improving the accuracy of incident response, and providing visibility into security operations, SOAR playbooks can help organizations to reduce the risk of security incidents and improve their overall security posture.
Here are some of the benefits of using SOAR playbooks:
If you are looking for a way to improve the efficiency and effectiveness of your security operations, SOAR playbooks are a valuable tool to consider.

JPCERT/CC is a valuable resource for organizations that are looking to improve their information security. By providing a variety of services, JPCERT/CC can help organizations to prevent, detect, and respond to computer security incidents.
Here are some of the things that JPCERT/CC does:
JPCERT/CC is a valuable resource for anyone who is interested in computer security. If you are a security professional, you can use JPCERT/CC’s resources to stay up-to-date on the latest security threats and to learn about new security technologies. If you are a business owner, you can use JPCERT/CC’s resources to improve your organization’s security posture. And if you are a student, you can use JPCERT/CC’s resources to learn about computer security and to get involved in the security community.
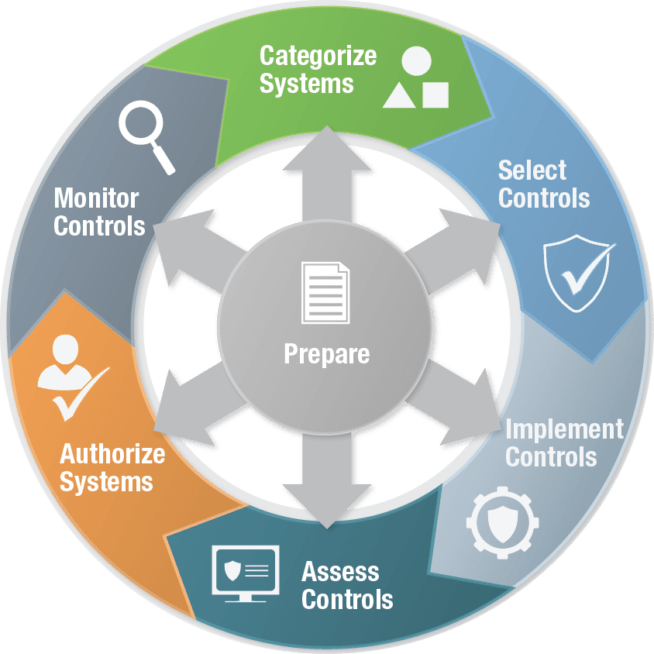
NIST RMF consists of the following 7 steps:
NIST RMF is a valuable tool for any organization that is looking to improve its information security. By following the NIST RMF, organizations can identify and mitigate risks to their information and systems, and improve their overall security posture.
Here are some of the benefits of using NIST RMF:
If you are looking for a way to improve your organization’s information security, NIST RMF is a valuable tool to consider.
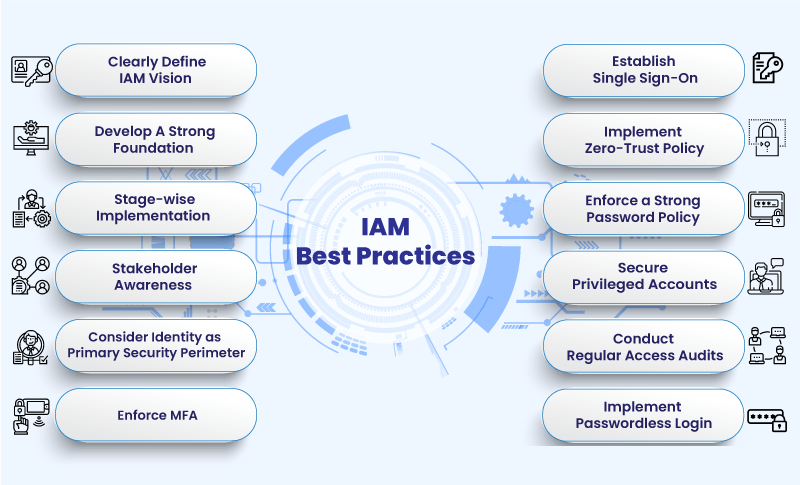
IAM helps organizations to ensure that only authorized users have access to sensitive data and systems.
IAM typically includes the following features:
IAM is an important part of an organization’s overall security strategy. IAM can help organizations to protect their data and systems from unauthorized access.
Here are some of the benefits of implementing IAM:
IAM is a valuable tool for organizations of all sizes. IAM can help organizations to improve their security posture, increase their efficiency, and reduce their costs.